The user management capabilities in Splashtop Secure Workspace provides administrators with multiple ways to manage users within the system. Let's explore the key aspects of user management:
User Provisioning
Administrators have various methods for provisioning users into the system. They can create users by specifying a username and password. Additionally, administrators can invite users by sending them an email invitation. By clicking the link in the email, users will be guided through the onboarding process, ensuring a seamless user experience. For organizations that enable single sign-on, users can be provisioned through SAML or OIDC (OpenID Connect) and OAuth 2 protocols. We will delve into the details of Identity Providers (IDPs) in a separate section of the documentation.
Roles and Permissions
When users are provisioned into Splashtop Secure Workspace, they are assigned specific built-in roles. Roles define the permissions for functionalities that users have within the system. Administrators can grant different role to an user based on their responsibilities and access requirements.
Roles and permissions
| User | Analyzer | IT Manager | Org Admin | Super Admin | Auditor | |
|---|---|---|---|---|---|---|
| Manage Organizations | ✓ | |||||
| Manage Access | ✓ | ✓ | read only | |||
| Manage IDPs | ✓ | ✓ | read only | |||
| Manage Connectors | ✓ | ✓ | read only | |||
| Manage Devices | ✓ | ✓ | read only | |||
| Manage Applications | ✓ | ✓ | ✓ | read only | ||
| Monitor Activities | ✓ | ✓ | ✓ | ✓ | ✓ | |
| Monitor own Activities | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ |
| Manage Personal Secrets | ✓ | ✓ | ✓ | ✓ | ✓ | read only |
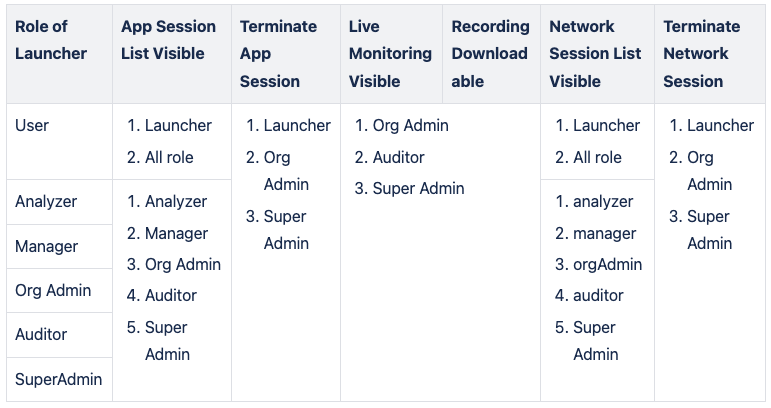
Session & Recording & Live Monitoring's Permission of Application
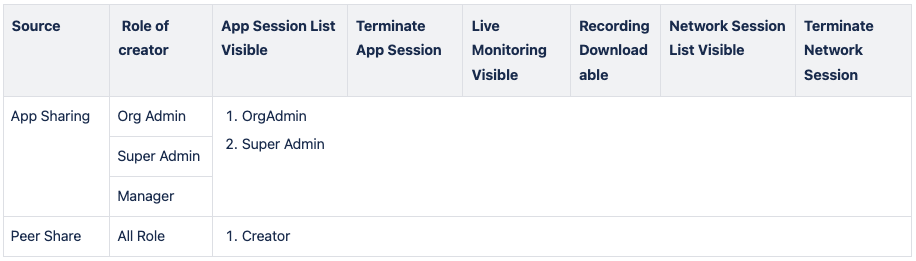
Session & Recording & Live Monitoring's Permission of App Sharing and Peer Share
In conclusion, User Management in Splashtop Secure Workspace offers versatile capabilities to effectively manage users within the system. Administrators can provision users through various methods, assign roles to define permissions, and leverage group management for streamlined access control.