Transforming Secure Access
Unleashing the Power of Splashtop Secure Workspace for Seamless Work from Anywhere Experiences
Introduction
Splashtop Secure Workspace is a cutting-edge solution designed to address the pain points faced by organizations in the era of digital transformation. With the increasing adoption of remote work and the growing complexity of network resources, applications, and credentials, enterprises, especially SMBs, are encountering numerous challenges. These challenges include user onboarding, technology availability, frictions caused by multiple point solutions, security and compliance requirements, lack of visibility, and connectivity issues. To overcome these hurdles, Splashtop Secure Workspace offers a comprehensive and secure environment for employees to work from anywhere, ensuring seamless access to network resources and services.
Pain Points and Challenges
From an Employee/End User Perspective
Traditional connectivity tools such as VPNs introduce several pain points for end users. VPNs are commonly used to access enterprise applications on private networks, but they often lead to slow internet access and hinder the performance of SaaS applications. Users face difficulties when trying to connect to multiple remote resources simultaneously or when encountering conflicts with IP addresses. Moreover, accessing applications through VPNs requires users to remember IP addresses and port numbers, which can be a significant challenge for non-technical employees. Other pain points include the inability to access resources in urgent situations when only a phone is available, difficulties in accessing region-specific office networks, and restrictions on VPN usage in certain network environments. The disconnection of various tools, such as VPNs and network client applications, as well as the need to manage information like IP addresses, ports, and credentials, creates friction for end users.
From an IT Admin Perspective
IT admins face challenges in onboarding and enabling users to work from anywhere. Provisioning and managing the infrastructure necessary to support high-performance network access across geographically distributed locations, such as firewalls, VPNs, site-to-site VPNs, or SD-WAN, require significant effort and resources. Managing access to a wide range of applications, both SaaS and private network applications, under a unified policy management framework is a complex task. IT admins often struggle with privileged access management, including sharing access without sharing passwords to critical systems or cloud applications. Managing access for third-party or internal users and securely sharing secrets or passwords is also challenging. In addition, integrating users and contractors from different identity providers, such as Azure AD or Okta to social platforms like Facebook or GitHub, poses difficulties. Enforcing application access requirements based on device security posture while allowing BYOD further complicates IT administration. Lastly, managing ever-changing access requirements while maintaining consistent security and policy enforcement adds to the IT admin's burden.
The Underlying Challenges of Access Management
The pain points experienced in access management can be traced back to certain fundamental root causes. Today, many organizations rely on a collection of disconnected point solutions to address their access needs. These solutions, including identity management, remote management and access systems, VPNs, firewalls, and secret vaults, are often implemented in a loosely integrated manner. This fragmented approach gives rise to several challenges and amplifies the pain points associated with access management.
One significant root cause is the lack of integration and cohesion among these disparate components. Each solution operates independently and has limited visibility into the complete access context. For example, the remote access solution may not have full knowledge of user entitlements stored in the identity management system, or the device and network security posture managed by endpoint management systems. This fragmented approach leads to a lack of comprehensive understanding and control over access requests.
Furthermore, the disconnected nature of these point solutions hinders seamless user experiences. Users often encounter multiple login prompts, cumbersome authentication processes, and a lack of clarity about their entitlements and available resources. This results in a suboptimal user experience that hampers productivity and satisfaction.
The siloed nature of these point solutions also leads to fragmented security measures. Each component operates independently, making it challenging to enforce consistent security policies and implement robust security controls across the entire access landscape. This fragmentation exposes organizations to security vulnerabilities and compliance risks.
Moreover, the manual tasks associated with managing these point solutions further contribute to the pain points. IT administrators often need to juggle multiple tools, perform repetitive tasks, and manually integrate workflows to address access requirements. This manual effort is time-consuming, prone to errors, and hinders operational efficiency.
To overcome these root causes and alleviate the pain points associated with access management, a new comprehensive and holistic strategy is required. Organizations need to transition from a legacy "best-of-breed" approach built around isolated technologies to an integrated and unified solution. This holistic approach should provide seamless integration, comprehensive visibility, and centralized control over access management, ensuring both security and user experience are prioritized.
Splashtop's Holistic Architecture
Splashtop Secure Workspace takes a holistic approach to address the pain points associated with access management. The architecture is designed to provide a comprehensive solution that considers the multiple factors involved in granting access. When a user establishes a successful access connection, it signifies that they possess the correct identity, entitlements, a device with compliant security posture, proper networking, and validated account and identity credentials for the target resource or service. These factors are interconnected and form the foundation of Splashtop Secure Workspace's general access management system.
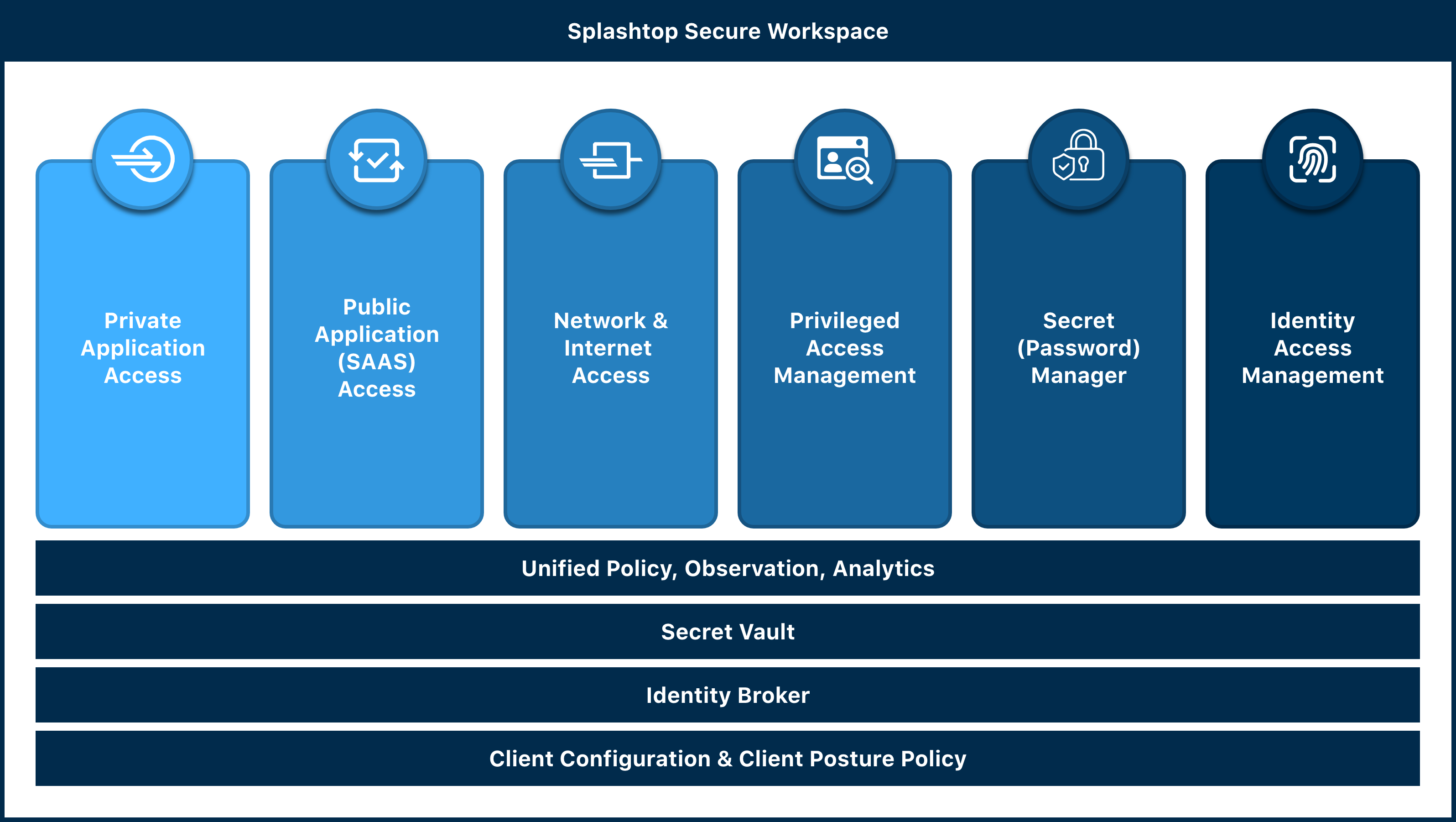
The architecture of Splashtop Secure Workspace ensures that these foundational layers—identity, device, networking, and secrets—are interconnected. This integration enables a complete and contextual view of access requests in any use case. For example, when a user requests access, the system can evaluate their identity and entitlements stored in the identity management system, device security posture managed by the endpoint management system, and network security posture. This comprehensive understanding of the access context allows for more effective and secure access control decisions.
The interconnected nature of Splashtop's Holistic Architecture brings numerous benefits. It creates an environment that enhances user experiences, delivering exceptional performance and uninterrupted access for employees, regardless of their location. Users can enjoy immersive and high-quality experiences throughout their work journey. Moreover, the architecture empowers organizations to implement robust security measures, including end-to-end Zero Trust principles and conditional access controls. This enables seamless and secure access to all applications, whether they reside on-premises, in the cloud, or are SaaS-based. As a result, organizations benefit from a comprehensive and highly effective security framework that enables users to access any application from any device with confidence.
Example Use Cases
Splashtop Secure Workspace supports a wide range of use cases, offering better user experiences, comprehensive IT and security control, and unprecedented capabilities compared to legacy solutions. Here are key use cases enabled by the solution:
All-in-one Workspace
Splashtop Secure Workspace provides an all-in-one user experience for managed devices and BYOD scenarios. The secure workspace desktop displays all the applications that users are entitled to use, including SaaS applications and enterprise network applications. Users can connect to these applications with a single click, and the workspace app automatically optimizes the networking experience by choosing the appropriate Point of Presence (POP) to connect to. The built-in password manager simplifies access by auto-filling target resource credentials. IT admins have the flexibility to customize the application launch process, such as automatically mounting SMB share drives upon connection.
For BYOD scenarios, Secure Workspace offers browser, browser extensions, and mobile app access to SaaS applications and commonly used remote applications like RDP, SSH, VNC, Telnet, and FTP.
User onboarding is a seamless and automated process, with activation via login or existing single sign-on (SSO) credentials. The personalized workspace, including applications, network access policies, client posture policies, and shared secrets, is automatically provisioned to users, enabling turnkey usage from anywhere.
Secure Privileged Access
Splashtop Secure Workspace simplifies the sharing of privileged access without sharing credentials. IT admins can conveniently share privileged access to private applications or SAAS accounts with individual users or groups. Users are prompted to choose the appropriate privileged account upon access. This capability ensures secure access to devices, servers, and SAAS applications that require privileged accounts, such as administrator or service accounts.
Secure Third-party Access
Secure Third-party Access is a crucial aspect of Splashtop Secure Workspace, providing organizations with secure and controlled access for external parties. This feature caters to scenarios where long-term contractors or external collaborators require access to specific resources or applications within the organization's environment.
For long-term contractors with Secure Workspace logins, IT admins can provide privileged access to these accounts.
Additionally, Splashtop Secure Workspace offers a convenient and secure shared link feature for granting temporary access. IT admins can define conditions such as schedules, passphrases, or other optional criteria to further control and restrict access. This flexibility allows IT admins to securely share resources with external parties, whether they are ad-hoc users or guests requiring temporary access.The shared link can be distributed through various means, making it easily accessible to the intended recipients. This feature streamlines collaboration with third-party entities, enabling them to securely access the necessary resources and applications within the organization's environment. IT admins have full visibility and control over these shared access links, ensuring compliance and security at all times.
Secure Internet Access
With Splashtop Secure Workspace, IT admins have the ability to set specific policy options for internet access on company devices. These policies can be tailored based on factors such as schedule, location, browser, operating system, and more. By defining access conditions, IT admins can ensure that employees can only access the internet during specified times or from approved locations.
Furthermore, IT admins can control the domains that employees are allowed or denied access to. This capability provides a powerful mechanism to protect employees from accessing potentially harmful or unproductive websites, mitigating security risks and enhancing productivity. By defining a whitelist or blacklist of internet domains, IT admins can enforce strict browsing policies based on the organization's security requirements and employee needs.
Secure Secret Access
Splashtop Secure Workspace offers organizations a secure and efficient solution for managing and accessing sensitive information. One of its key features is the Secure Secret Access, which includes a comprehensive organization vault shared among administrators and individual vaults for each user.
IT administrators can securely store privileged accounts in the secret vault, ensuring that only authorized individuals have access to these critical resources. Moreover, the secret vault facilitates privileged access to private network resources, allowing the platform to utilize the credentials from the vault to authenticate on behalf of users without directly sharing the credentials with them. To further enhance security, the secret vault is protected by robust access policies, empowering administrators to define specific conditions and permissions for accessing the stored secrets.
End users can leverage the secret manager available within the Secure Workspace browser extension, desktop application, and mobile app. This powerful tool enables users to securely and conveniently access and auto-fill passwords for the resources they are authorized to use. As a result, users are relieved from the burden of remembering or manually inputting complex passwords, leading to improved efficiency and a reduced risk of password-related security breaches.
In addition, Secure Secret Access provides organizations with a secure and user-friendly solution for sharing secrets among employees or guest users. By leveraging the secret manager and the access policies, organizations can securely share sensitive information while maintaining control over who can access the secrets and under what conditions.
Secure Access Automation
Splashtop Secure Workspace provides IT administrators with powerful automation capabilities, enabling them to efficiently and securely automate remote access to target resources and systems.
IT admins can leverage the rich APIs and command-line interface (CLI) tool offered by Splashtop Secure Workspace to automate various aspects of remote access. The rich APIs allow for seamless integration between Splashtop Secure Workspace and other systems and applications within the organization's IT infrastructure.
By utilizing the rich APIs, IT admins can programmatically interact with Splashtop Secure Workspace, automating tasks such as provisioning access, managing authentication processes, and configuring resource settings. This integration with existing systems streamlines workflows, improves operational efficiency, and enhances overall productivity.
Furthermore, the CLI tool provided by Splashtop Secure Workspace enhances automation possibilities even further. IT admins can leverage the CLI tool to establish secure connections to remote targets, enabling them to invoke services or execute commands on the remote systems in the same manner as they would for local network automation.
Secure Access Mission Control
Secure Workspace empowers IT administrators with a wide range of horizontal controls to support the aforementioned use cases and beyond. These controls include:
- Device enrollment and security posture control: IT admins can enforce the enrollment of devices and assess their security posture before granting access. This ensures that only authorized and secure devices can connect to the network, reducing the risk of compromised access.
- Organization-level unified policies: Secure Workspace allows IT admins to establish unified policies at the organization level. These policies cover various aspects such as authentication, authorization, application access conditions, secret access conditions, and web filtering. By implementing these policies, organizations can ensure consistent and standardized access management practices throughout the entire organization.
- Application and secret-level conditional access policies: IT admins have the flexibility to define conditional access policies at the application and secret levels. These policies consider factors such as user groups, time, location, and browser. By applying these granular policies, IT admins can control access permissions based on specific conditions, providing a higher level of security and access control.
- Real-time session management: Secure Workspace equips IT admins with real-time session management capabilities. They can monitor and manage active user sessions, terminate sessions if necessary, and enforce session recording for auditing and compliance purposes. This real-time visibility and control over sessions enhance security and facilitate efficient session management.
Moreover, the platform offers comprehensive visibility through event and session video recording. By leveraging rich telemetry data, organizations gain insights into various events and can review session recordings when necessary. This comprehensive visibility enhances security monitoring and enables organizations to maintain a strong security posture.
Conclusion
Splashtop Secure Workspace offers a holistic solution to address the pain points of modern work environments. By providing seamless, secure, and frictionless access to network resources and services, it enables employees to work from anywhere. The comprehensive architecture and innovative approach allow organizations to prioritize user experience while maintaining stringent security measures. With features like all-in-one workspaces, secure privileged access, third-party access, secure internet access, secret management, access automation, and mission control, Splashtop Secure Workspace stands as a powerful solution for the challenges of the hybrid workplace.