# Splashtop Secure Workspace Integration with Microsoft Teams
Overview
Splashtop Secure Workspace (SSW) for Microsoft Teams is designed to streamline the process for regular users to request access to SSW applications while enabling administrators to quickly review and respond to these requests. This integration enhances communication and efficiency in managing application access within an organization.
Process Guide
1. Initial User Setup
-
Accessing Splashtop Secure Workspace: Users need to first open the Splashtop Secure Workspace within the Teams applications.
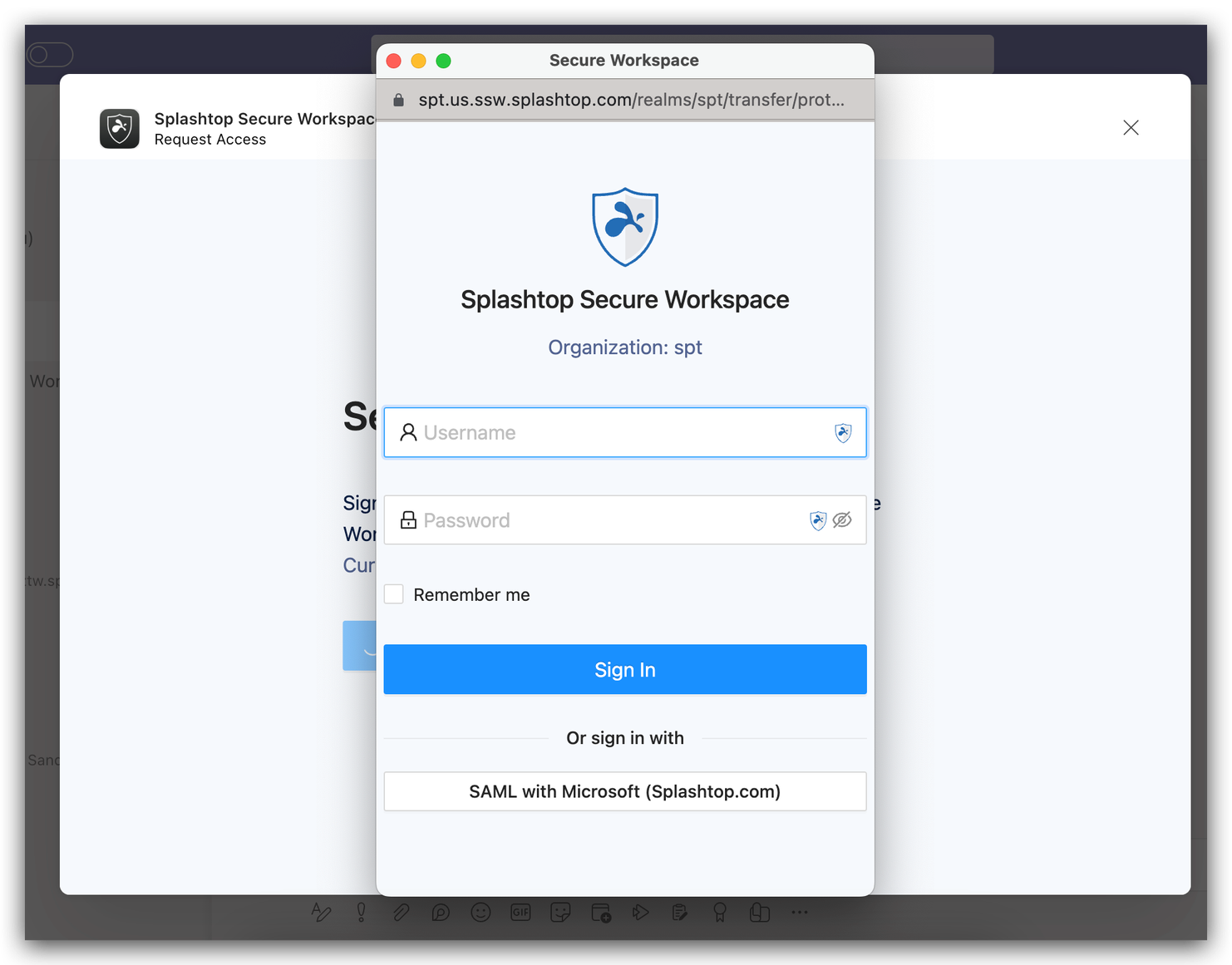
-
User Authentication: Users should log in to their account using either their username and password or through Single Sign-On (SSO).
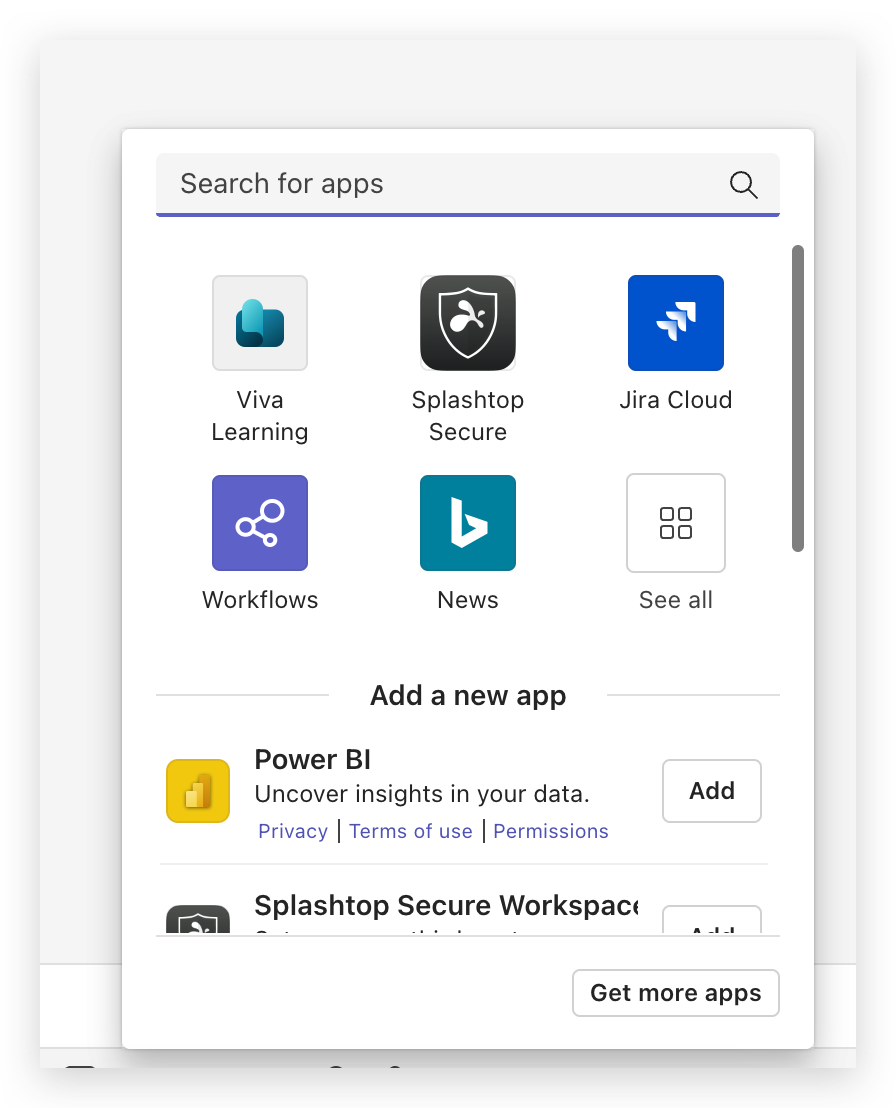
2. Requesting Application Access
- Accessing the Dashboard: After logging into the Splashtop Secure Workspace (SSW) within Microsoft Teams, users will be presented with a dashboard. This dashboard displays all the SSW applications for which they can request access.
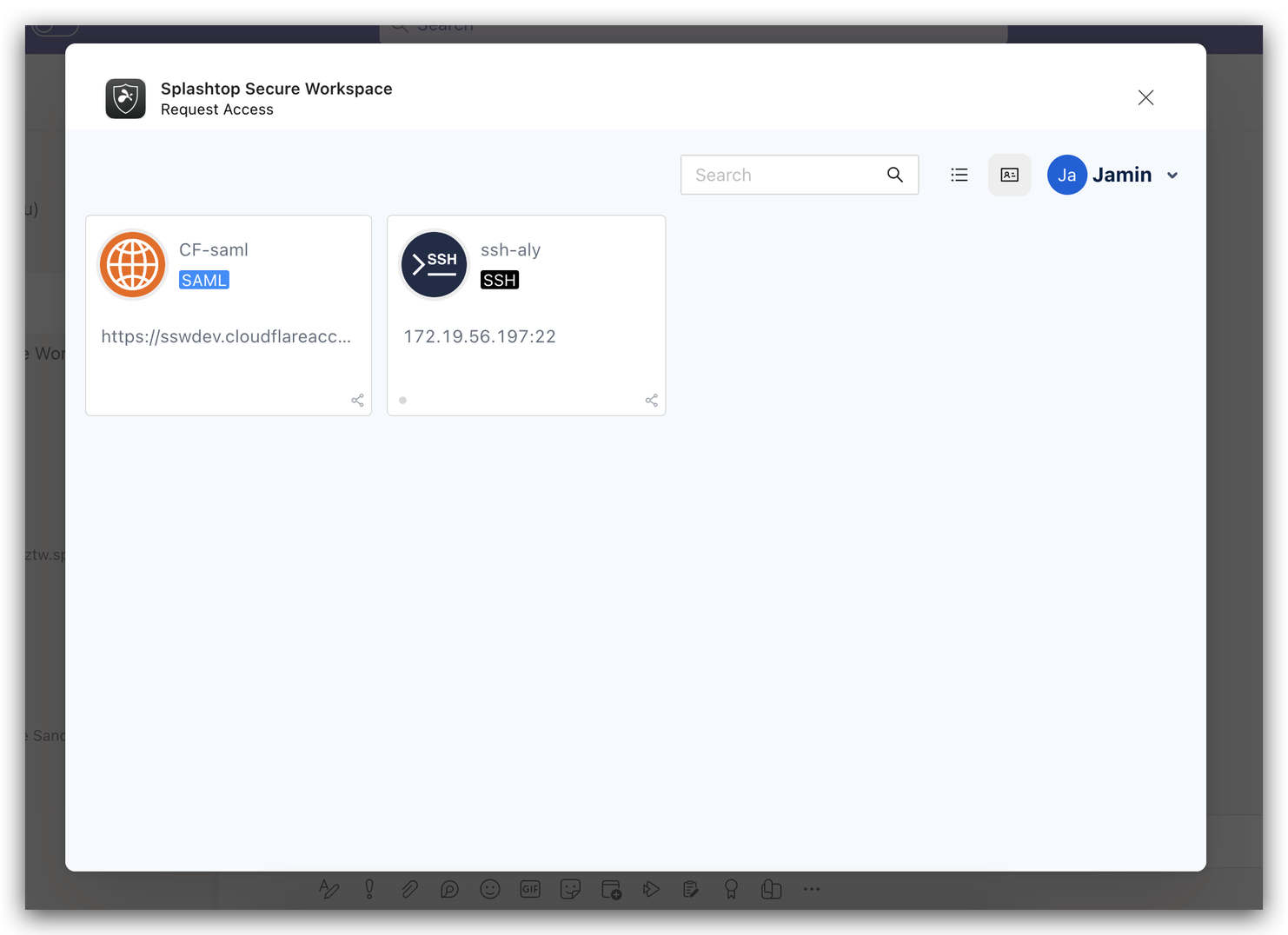
- Application Request Process:
- To request access, users simply need to click on the card of the desired SSW application displayed on their dashboard.
- This action initiates a request for access to the specific application, which is then sent to the relevant administrator for approval.
3. Administrator Actions
- Review and Decision: Administrators, upon receiving a request, need to log into SSW to review it. They have the option to either grant or deny access.
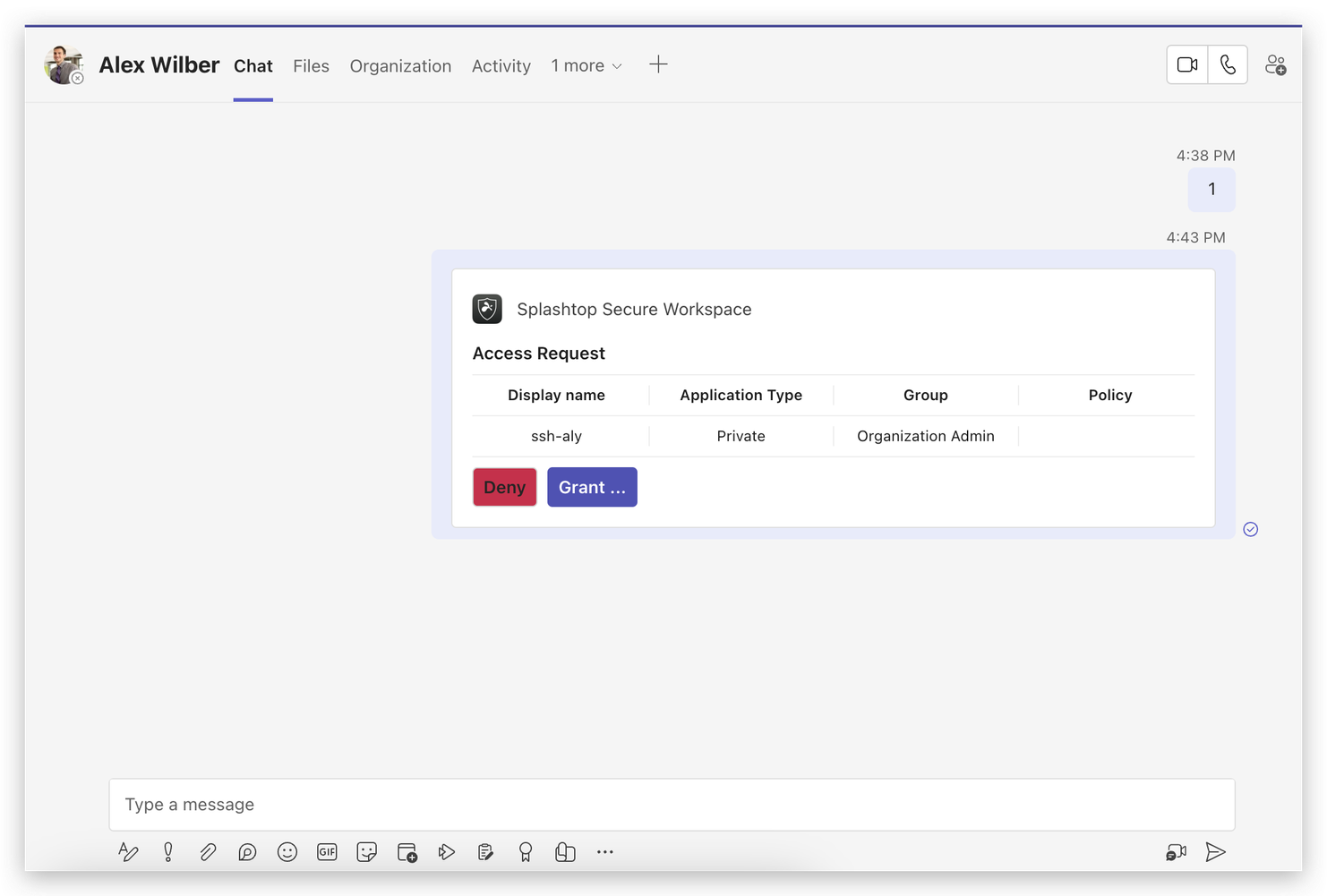
4. Granting Access
-
Automated Application Sharing: Once an administrator approves a request, the SSW app automatically creates a sharing setup for the requested application.
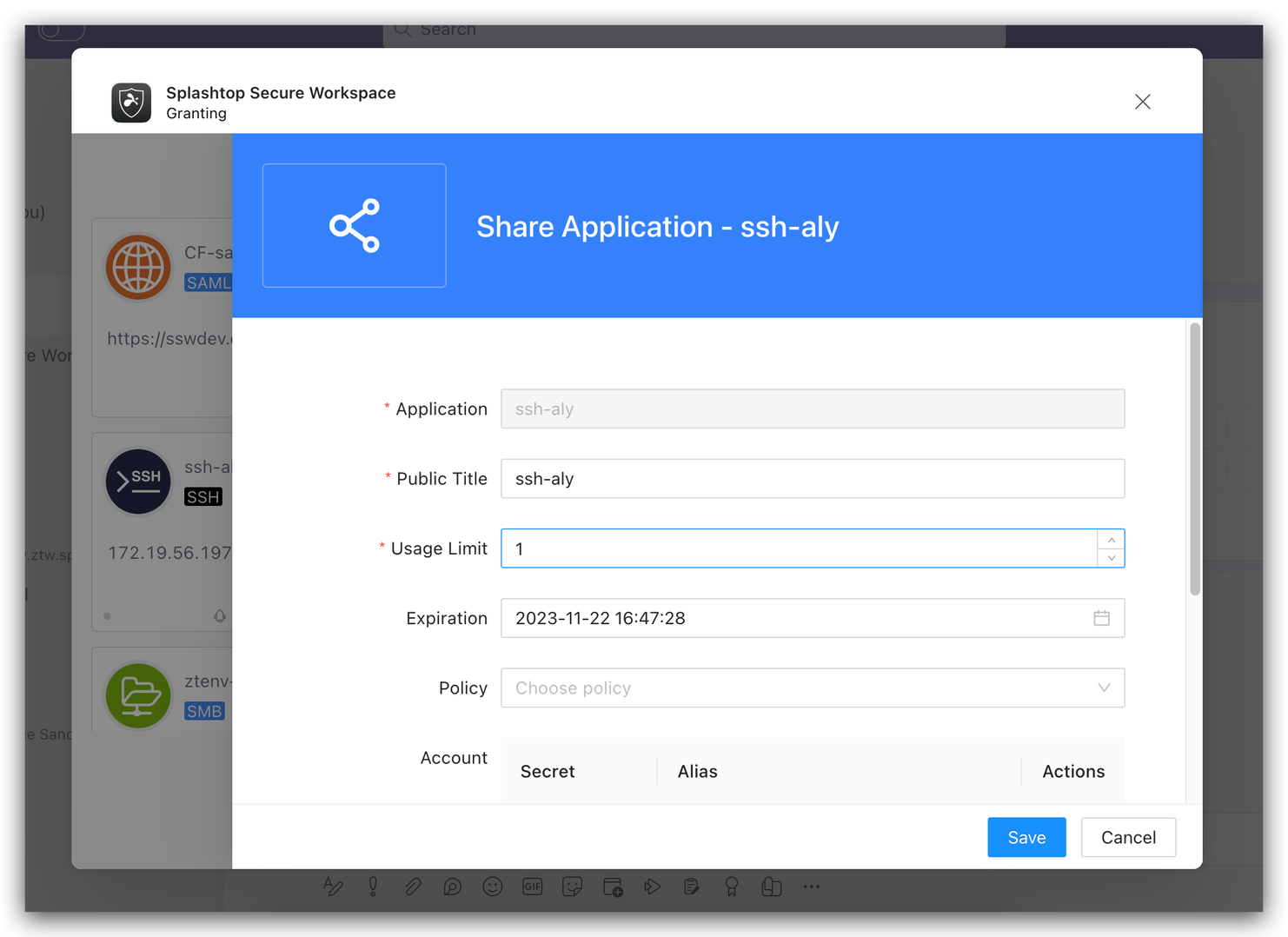
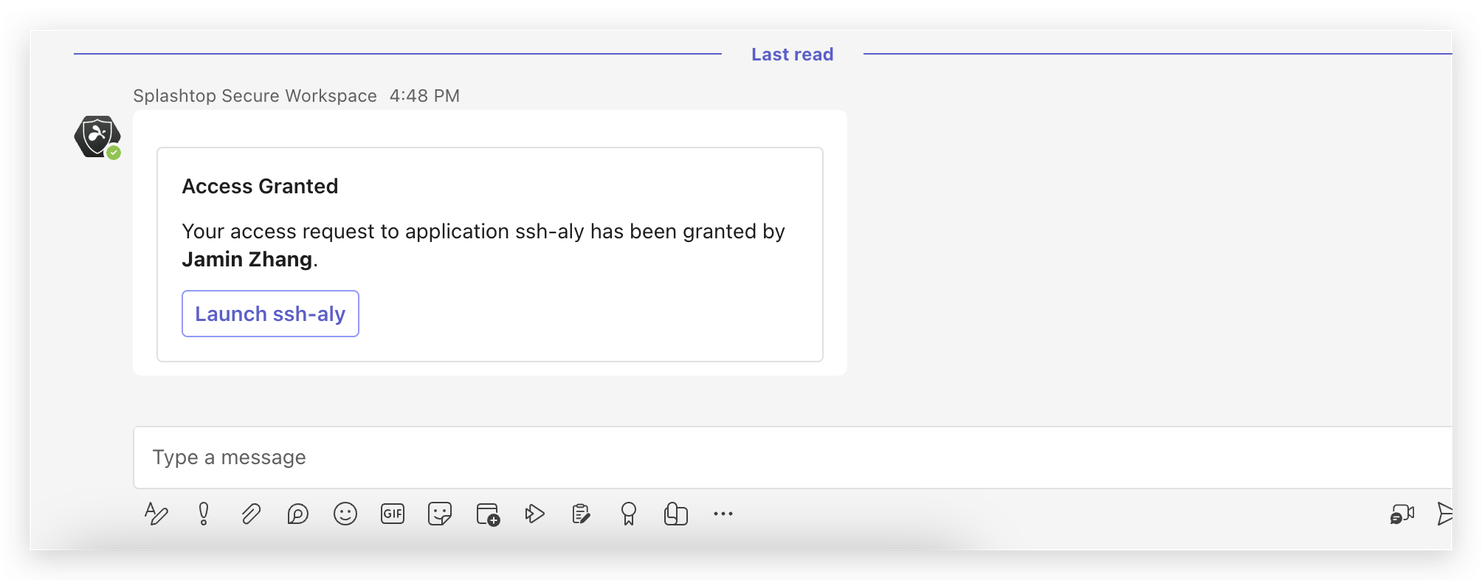
-
Access Notification: The requester receives a notification card through Teams. By clicking on the button in this card, they gain access to the requested resource.
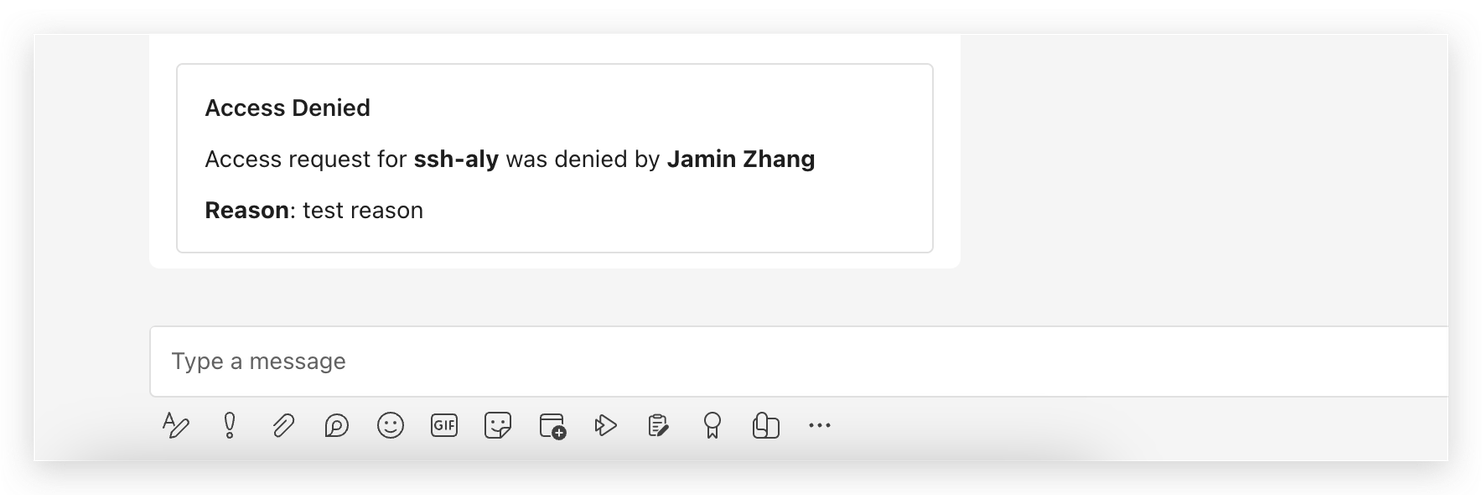
5. Denying Access
-
Reason for Denial: When denying a request, administrators are required to specify the reason for the denial.
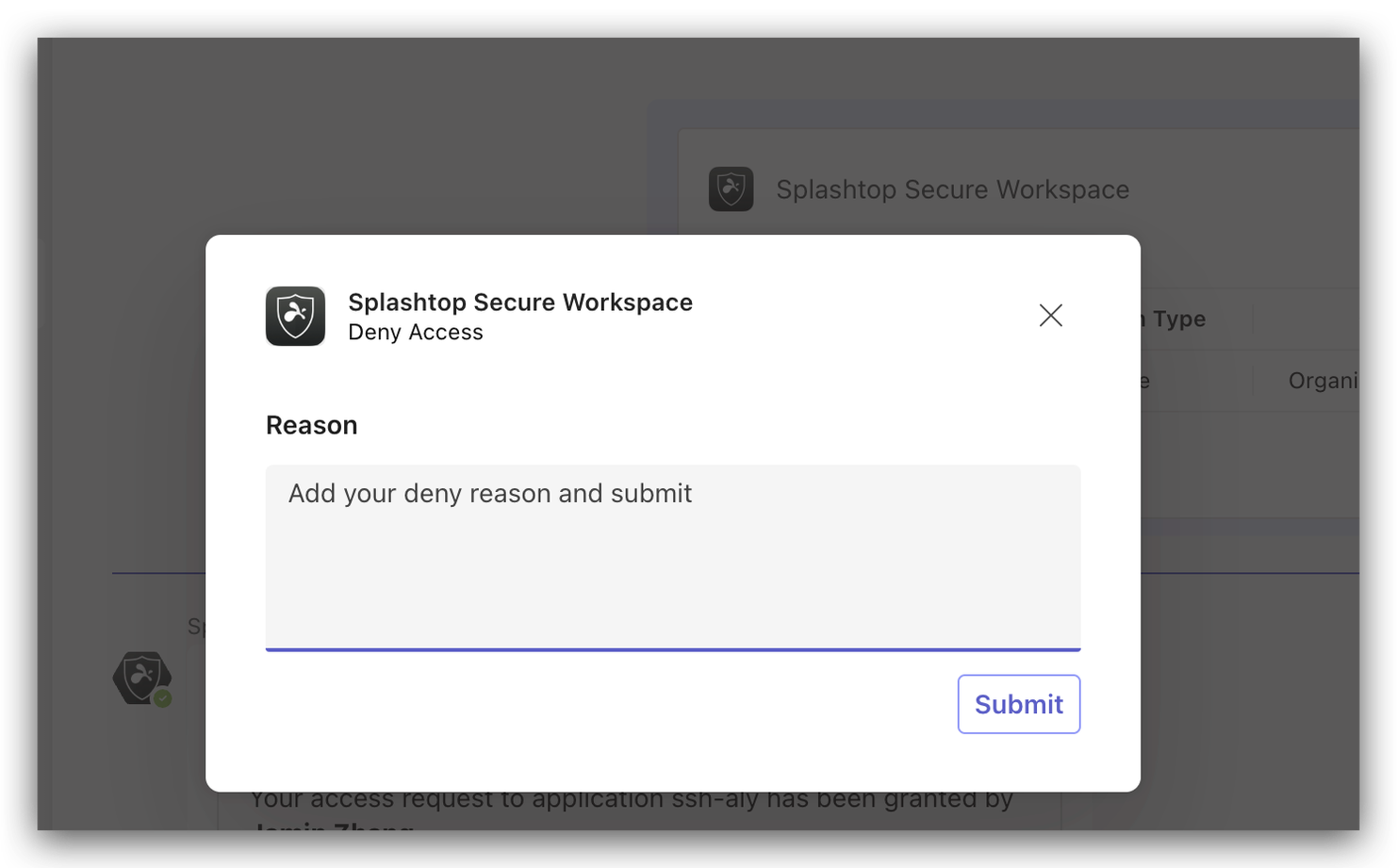
-
Notification of Denial: A denial card is then sent to the requester, informing them of the decision and the reason behind it.