The Sessions section in Splashtop Secure Workspace allows you to monitor and manage active user sessions within your workspace environment. This feature provides real-time visibility into user activities and enables you to ensure the security and integrity of your workspace.
Monitoring Active Sessions
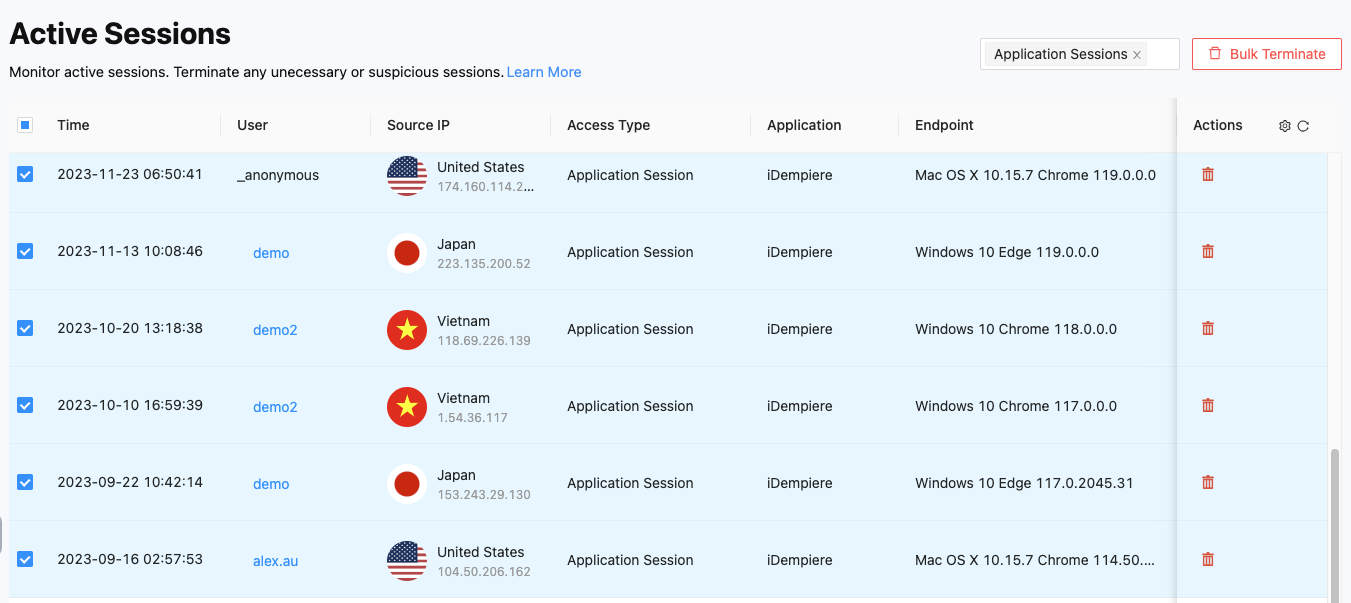
On the Sessions page, you can view a list of active sessions with the following information for each session:
- Time: The timestamp indicating when the session started.
- User: The username associated with the session.
- Source IP: The IP address from which the session originated.
- Access Type: The type of access used to establish the session (e.g., Vault Sessions, Application Sessions, Network Sessions).
- Application: The specific application accessed in the session.
- Endpoint: The endpoint or device from which the session is initiated.
- Actions: The available actions for each session.
Live Monitoring:
When an application has enabled Live Session Monitoring, administrators can actively observe user behavior in real-time by simply clicking the  button when active sessions are present for that application.
button when active sessions are present for that application.
Note: Currently, Live Session Monitoring can only be enabled for Private Applications of types TELNET, SSH, K8S, RDP, VNC and Cloud Browser Applications. Furthermore, administrators can engage in real-time monitoring only when the session's access type is browser.
Terminating Sessions
If you identify any unnecessary or suspicious sessions, you can terminate them directly from the Sessions page. Simply click the  button in the Actions column for the respective session, and the session will be immediately ended.
button in the Actions column for the respective session, and the session will be immediately ended.
Bulk Termination
In case you need to terminate multiple sessions simultaneously, you can utilize the Bulk Terminate feature. Select the desired sessions by checking the corresponding checkboxes and click the "Bulk Terminate" button located at the upper right corner of the page. This allows you to quickly terminate multiple sessions in one action, streamlining your session management process.
Filtering Sessions
To focus on specific types of sessions, you can use the filter options available on the page. By selecting the desired access type (e.g., Vault Sessions, Application Sessions, Network Sessions), you can narrow down the list and view sessions that fall under the chosen category.
The Sessions section provides a centralized view of active user sessions, empowering you to monitor session activities, terminate suspicious sessions, and ensure the security and compliance of your workspace environment.