Introduction
Splashtop Secure Workspace is a comprehensive and extended SASE (Secure Access Service Edge) platform designed to manage secure access to networks and applications for IT environments, including third-party, privileged, and employee access. It leverages advanced Zero Trust principles to enhance operational efficiency and security performance.
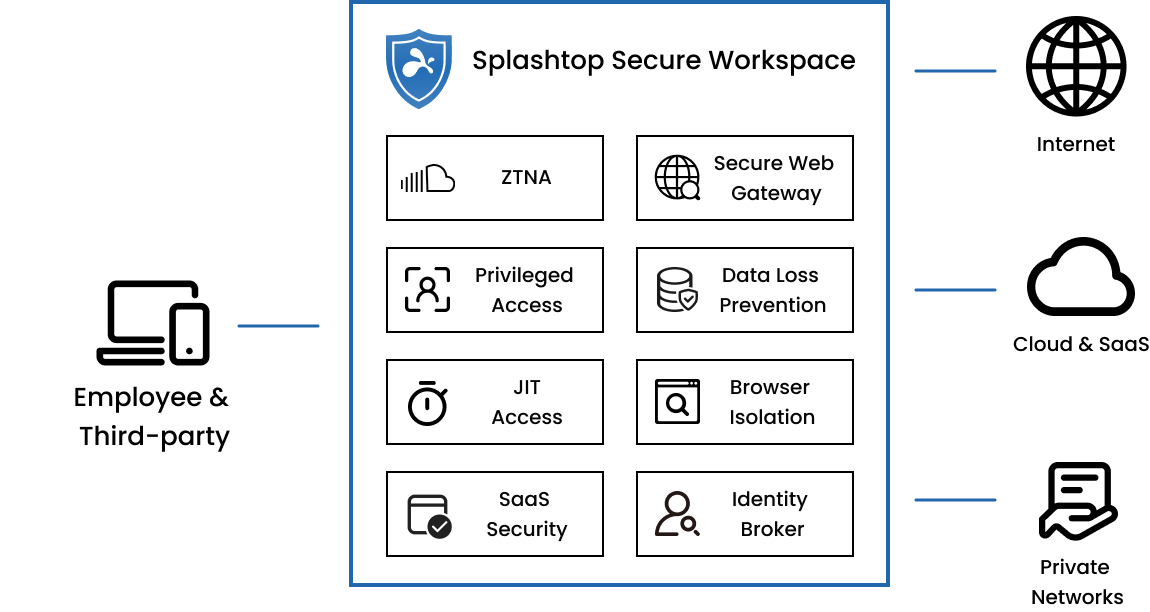
Key Features and Capabilities:
Zero Trust Network Access (ZTNA)
- Superior Alternative to VPNs: ZTNA offers a secure alternative to traditional VPNs, providing faster, safer, and more resilient network access. It validates user and device access based on identity, device posture, and contextual factors, ensuring secure application access on any network.
- Access Validation and Enforcement: The platform supports BYOD policies across managed and unmanaged devices, applying Zero Trust policies to secure access for hybrid workloads. This ensures that only authenticated and authorized devices can access the network, reducing the risk of unauthorized access and data breaches.
- Clientless and Device Client Access: ZTNA accommodates both clientless access and device clients, making it versatile for various user scenarios and enhancing the flexibility of access management.
Privileged Access Management (PAM)
- Enhanced Credential Security: PAM secures privileged account credentials with invisible injection, live monitoring, and session recording, ensuring that credentials are never exposed to users.
- Automated Credential Management: The platform automates the management and rotation of credentials for Windows/Active Directory, integrating with a secure Secret Vault for credential injection. This reduces the risk of credential theft and simplifies the management of privileged accounts.
- Zero Touch Provisioning: PAM enables seamless infrastructure integration without firewall or routing changes, featuring application auto-discovery for quick and efficient setup.
Just-in-Time and On-Demand Access (JIT)
- Dynamic and Secure Access: JIT access provides temporary access to applications and data as needed, reducing the window of opportunity for unauthorized access or internal misuse. This feature is crucial for managing access for third-party vendors, contractors, and partners.
- Integration with Collaboration Tools: JIT access seamlessly integrates with tools like Microsoft Teams and Slack, enhancing productivity and security by ensuring zero standing privileges and user-friendly access.
- Flexible Access Methods: JIT access can be provided via hyperlinks or QR codes, supporting various access types including Zero Trust Network Access, Privileged Access, and Remote Browser Isolation. This flexibility ensures secure access across different
Secure Internet Access (SWG, DNS, RBI)
- Comprehensive Threat Defense: Secure Internet Access combines DNS/URL filtering, cloud controls, SSL inspection, DLP, anti-malware, and RBI to enforce Zero Trust across all internet activity. This comprehensive threat defense ensures that all internet traffic is secure and monitored for potential threats.
- Endpoint-Based Secure Web Gateway: Shifting the Secure Web Gateway to the endpoint ensures a faster, smoother user experience without traffic redirection, enhancing the reliability and performance of internet access.
- Extended Control Range: The platform extends SWG, DNS, and RBI controls to encompass ZTNA and private application access, providing broader security coverage and more robust protection against threats.
Comprehensive SaaS Security
- Zero Trust for SaaS: The platform implements Zero Trust security measures to protect SaaS applications from unauthorized access, ensuring that only authenticated and authorized users can access sensitive information.
- Streamlined Identity Management: It facilitates efficient identity management with SSO, MFA, and conditional access, supporting BYOI for third-party integrations. This ensures that identity and access management is seamless and secure across all SaaS applications.
- Enhanced Cloud App Security: The platform provides comprehensive control over cloud applications with CASB and DLP services, ensuring compliance with data protection laws. It integrates PAM and RBI for secure, monitored access to SaaS platforms, enhancing overall security and compliance.
- Integrates Privileged Access Management (PAM) and Remote Browser Isolation (RBI) for a more secure approach, ensuring secure, monitored access to SaaS platforms.
Monitoring and Telemetry
- Real-time Insights and Analytics: The platform offers extensive monitoring capabilities, providing real-time session management and comprehensive security analytics. This allows administrators to track and manage access effectively, detecting and responding to potential security threats proactively.
- Visibility into Access Requests: Detailed insights into access requests help maintain control over the network, ensuring that only authorized access is granted and any anomalies are quickly addressed.
Use Cases:
- Streamlining Employee Onboarding and Offboarding: Splashtop simplifies the IT process for onboarding new employees by automating the provisioning of access to essential applications. The platform also enables quick revocation of access when employees leave the organization, ensuring security and compliance.
- Secure, VPN-Free Access Across Hybrid and Multi-Clouds: The platform provides secure access to private applications and resources across various environments, eliminating the need for VPN setups. This reduces the risk of cyberattacks and improves user experience by simplifying access management.
- Secure and Convenient Privileged & Third-Party Access: Splashtop offers a holistic approach to third-party access, providing secure and controlled access to corporate resources for auditors, contractors, and vendors. This ensures that third-party access is temporary, secure, and auditable, enhancing overall security.
Key Benefits:
- Simplified IT Operations: Reduces the complexity and overhead associated with managing diverse access needs and security protocols, streamlining IT operations and enhancing productivity.
- Enhanced Security and Compliance: Ensures that all access is secure and compliant with industry standards, protecting sensitive information and reducing the risk of data breaches.
- Improved User Experience: Offers a seamless user experience across different access scenarios, enhancing productivity and satisfaction without compromising security.
Conclusion
Splashtop Secure Workspace is a comprehensive solution for managing secure access across various IT environments. With its robust feature set and flexible deployment options, it addresses the diverse needs of modern organizations, ensuring security, compliance, and operational efficiency.